This is the fourth and final blog post in a series that discusses discrimination and harassment in cyberspace, its perpetrators, and its consequences. The first post, “Identity and Ideas,” is available here. The second post, “Anonymity and Abuse,” is available here, with a short addendum here. The third post, “Privilege and Passivity,” is available here.
In my final post, I’ll discuss some of the options for people targeted by identity-based online harassment. I intend this post to complement the broader social responsibilities I outlined in my previous post.
One of my starting premises is that there isn’t a “right” way to respond when you are the target of identity-based online harassment. People who experience such harassment have a range of legitimate reactions, and differences in individual circumstances may dictate the best approach for a given individual. I’ve tried a number of these options myself, and I’ll share my experiences–not as a definitive assessment of the merits of each option, but simply as a way of highlighting some of the potential advantages and disadvantages.
Before I do that, I want to address a point with which some readers seem to struggle. By calling attention to identity-based online harassment, I am not denying that some people who engage in such harassment, and who have engaged in such harassment of me, also have substantive things to say. What I am saying is that the mere fact that people have something substantive to say doesn’t entitle them to engage in identity-based harassment, nor does it excuse them from turning a blind eye when others do so in threads they start or on blogs they administer. Lots of infamous people have had lots of substantive things to say–Ted Kaczynski, also known as the Unabomber, is one example. That doesn’t mean these people should be excused for the hateful ideas intertwined with their substantive ones. My point is obviously not that anonymous online harassment is equivalent to, for example, a nationwide bombing campaign. The point is that having substantive things to say doesn’t give you a free pass to spew racism and misogyny, and that criticizing people for refusing to engage substantively in forums that tolerate such harassment is a weak attempt to deflect attention from the harassment itself.
With that said, I’ll move on to some strategies for dealing with identity-based online harassment.
1. Ignore.
Many harassers have short attention spans, and will move on if you ignore them. Certainly this has happened with respect to some of the people who have posted racist and sexist comments about me. Sometimes, however, for whatever reason, one or more harassers becomes really fixated on you. I waited for over a year for my most persistent harasser to move on. He showed no sign of doing so. That’s when it might be time to take other action.
Even if you ultimately find it impossible to completely ignore pervasive harassment, there are ways of limiting its salience to your daily life. As a colleague suggested to me, one can ask a trusted friend or family member to monitor the forums where harassment takes place. I found this advice very useful. Alternatively, one might choose to visit certain sites only occasionally to check for statements that contain an imminent threat.
I want to emphasize that it’s not a sign of personal weakness or mental frailty if you’re unable to ignore identity-based online harassment targeted at you. The claim that women and people of color are “too thin-skinned” when they don’t overlook racist and misogynistic remarks is an old standby, but that doesn’t make it true. Perhaps it would make things easier if everyone could ignore the bad things said about them. But when ignoring is impossible, there are other options.
2. Engage.
Other people find engaging with harassers to be empowering, productive, and even enjoyable. Bina Shah, for example, offers useful advice for smacking down trolls on twitter. Linda Tirado, who writes about poverty under the name Killer Martinis, often takes a different approach, responding to hysterical commenters with dignity and empathy (see here for an example, particularly the first comment and response).
My own limited experience with engaging with harassers have been mixed. The reality is that, like many people, I have minimal time to engage with anonymous and pseudonymous purveyors of hate speech in poorly-read forums. As something of an experiment, I posted two brief comments in one forum, which produced an entertaining outburst of juvenile rage. (One of my favorites: “Lady Leong, this isn’t Afghanistan! You can’t come in here, drop a few bombs, and then leave!”) The downside, of course, is that harassers get angry when someone calls out their unacceptable behavior, and that can produce more harassment.
3. Use the law.
As I discussed in my previous post, we need a legal mechanism that wholly addresses the problem of identity-based online harassment. Right now, such a mechanism doesn’t exist. There are, however, various other legal doctrines that can address some of the harms of identity-based online harassment. None of this is meant as legal advice, but here are some legal options that may be worth considering in individual situations:
First, if online harassment includes credible threats to your safety or the safety of those close to you, it becomes a matter for law enforcement. I am fortunate that I have not experienced this firsthand, with the exception of one arguably threatening phone call from a blocked number, but other people certainly have experienced awful threats of rape and other violence.
Likewise, many states either have criminal cyberstalking or cyberharassment statutes that may cover identity-based online harasssment, and when laws specific to cyberspace are unavailable, more conventional criminal stalking and harassment statutes may apply. A recently-updated list of such statutes appears here. The scope of such laws varies considerably, so it’s important to examine the particularities of your jurisdiction, but some of them are quite useful. Moreover, it is not necessarily an obstacle if a harasser is in a different state than you; many statutes explicitly provide that if an electronic transmission is either sent or received in a particular state, the statute applies.
Copyright law can provide another vehicle to address identity-based online harassment. I succeeded in having a blog composed of pictures of me taken without permission from various online sources removed on the ground that it violated my copyright. I also succeeded in having thread containing a 1000-word cut and paste of my writing, with no additional commentary, removed from a website where it provoked an outburst of racist and sexist vitriol. I accomplished this by sending take-down notices, which non-lawyers can read more about here. Fair use is, of course, a defense, but it would likely be unavailing in situations where, for example, harassers simply copy and paste photographs or large portions of written material and there is nothing transformative about the use of the material. Moreover, website administrators will sometimes remove content even when fair use is debatable if the use in question is racist, sexist, or otherwise harassing.
And finally, defamation law can provide recourse if the statements about you are false and harmful to your reputation. (“She slept with someone to get her job” is an example.) Defamation law is notoriously slippery, and there are various practical obstacles to lawsuits that one must overcome. But in some situations it may be the best alternative. The Electronic Frontier Foundation offers a useful brief summary of defamation law that can provide a starting point for someone who thinks that she has been defamed.
4. Investigate.
A lot of harassers are anonymous, but others write under pseudonyms. Sometimes pseudonymous harassers and abusers build up entire personalities around their pseudonymous identities–for example, Violentacrez on Reddit, the instigator of popular subreddits “Creepshots” and “Jailbait”, later unmasked as Michael Brutsch.
Many pseudonymous people who engage in identity-based online harassment are trying to have it both ways. That is, they are trying to have the benefits that come with having a known identity–the community recognition; the ability to form relationships with others; the claim to speak authoritatively on certain topics–as well as the benefits associated with anonymity–namely, the ability to avoid any consequences for racist and misogynistic comments in real life.
I encountered several such pseudonymous individuals in my own experience with online harassment. Once I began paying attention to the various repeat players, certain rather disturbing preoccupations emerged. For example, one pseudonymous commenter stated the following* about a recent female law graduate:

I hope I don’t have to explain why fantasizing about exploiting a recent law school graduate’s financial vulnerability to perform a violent sexual act is profoundly troubling. Likewise, in previous posts, I’ve already referenced one of this particular commenter’s remarks about me, and noted that such a comment would constitute harassment in the workplace:

This specific comment is just one example; I’m making no effort to publicize all of them. Over the course of about fifteen months, this particular harasser commented about me approximately 70 times on at least five different websites, frequently remarking on my physical appearance. He started several derogatory threads devoted exclusively to me, in which other commenters also targeted me with racist and sexist harassment. He wrote two lengthy plays about me. The threads he started often attracted dozens or even hundreds of comments. His sustained attention to me also incited other pseudonymous members of a blog where he often posts to author lengthy racist and sexist posts about me, which, again, often attracted large numbers of comments about me, including comments from him. Moreover, he wrote offensive profiles of a dozen other law professors who were–so far as I could tell, with one exception–all women or people of color or both. And, of course, these were just the comments under his pseudonym. It would not surprise me to learn that some of the many anonymous comments about me were also by him, although I haven’t taken the time to investigate this. This sustained attention and the ideas it contained became increasingly disturbing to me, and eventually I decided to figure out who he was.
Many people underestimate the ease with which they can be linked with their anonymous or pseudonymous comments on the Internet. Kashmir Hill has described how to bait and catch a troll using a blog and IP address tracker–a relatively straightforward process even for someone with only limited technological capabilities. For many people who experience online harassment, such techniques could provide a viable option.
With respect to my various harassers, even this rudimentary technique turned out to be unnecessary. The pseudonymous individual I mentioned above had posted specific information about his alma mater, the city where he lived, his job, various professional organizations to which he belonged, and other miscellaneous information. It took fifteen minutes to find out who he was using google and other publicly available databases. The result was troubling in itself: he was a public defender in his late forties who apparently has nothing better to do than harass an untenured professor.
It was equally easy to identify a few other people who posted about me. Indeed, someone had created a website dedicated to identifying one of them two years before he first crossed my radar.
There are a few lessons here. One is that even in the online world harassers often feel compelled to develop continuous and stable personalities, perhaps as a way of compensating for the social deficiencies in their actual lives. Another is that a lot of harassers are repeat offenders–that is, if someone is harassing you, odds are that you aren’t the first.
Particularly if identifying a pseudonymous harasser is minimally time-consuming, it can be a reassuring exercise. I was glad to know that none of the pseudonymous harassers I identified were people who I had met or who lived anywhere near me. Investigating and identifying a harasser is also valuable because it opens up other possibilities for addressing the situation, to which I will now turn.
5. Confront.
After I discovered the identity of my most persistent harasser, I decided to give him a call, which is something that adults do when they have a disagreement to discuss. I did this for several reasons. One was that I wanted to talk to him so that I could try to understand why an untenured professor he had never met could become the subject of a year-plus obsession. Another reason was pure curiosity. I have always been interested in what causes people to hate one another–or, at the very least, to write hateful things about other people, especially those they have never met. But the main reason was simply that I truly wanted to give him the benefit of the doubt. People’s lives are complicated by mental illness, loneliness, personal hardship, and grief. Although I have tried without success to find a definitive source for the saying “be kind, for everyone you meet is fighting a hard battle,” the words resonate with me and I try to live them. My hope was that the person who had written so many hateful things about me was a good person who–prompted by difficult personal circumstances–had made a mistake.
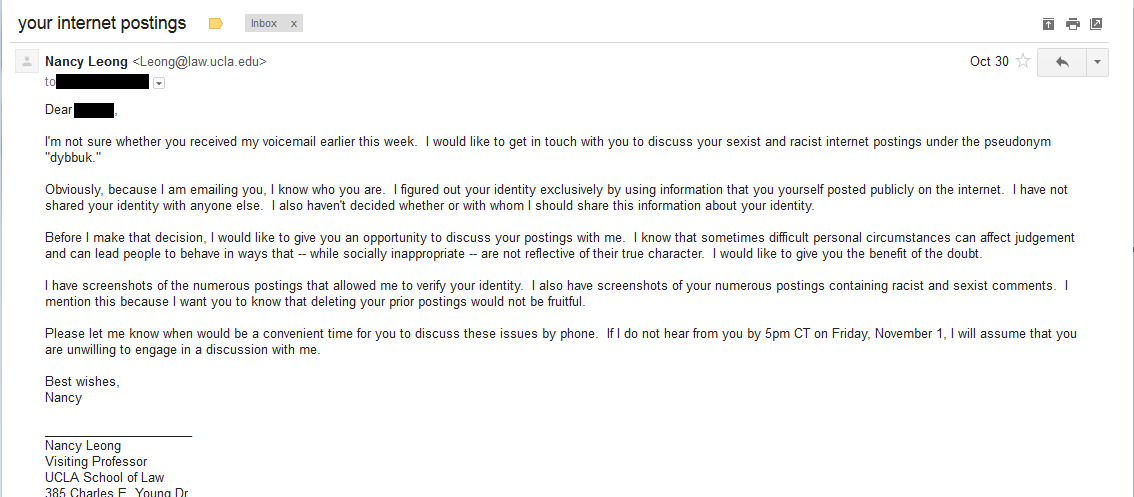
To my regret, my harasser refused to speak to me. I called him at his office (once) and left a message with the person (not him) who picked up the phone simply leaving my name and number and asking him to call me. He didn’t call back. A few days later I emailed him (once), explaining that I had identified him and that I wished to discuss his Internet posting activities. The email was difficult to write. It triggered emotions relating to an experience confronting a person who abused me many years ago. I did my best to keep the email polite and professional and–to the extent I could–I tried to express some sympathy for circumstances in his life of which I might not be aware. If anyone finds themselves in similar circumstances, they are welcome to borrow any of the language of my email (larger image available here):
Of course, I can only guess at the real reason my harasser refused to speak with me. Was he really afraid to speak with an untenured professor nearly fifteen years his junior who had already explicitly stated that she wished to give him the benefit of the doubt? If so, why? His refusal leads me to think that perhaps John Kang’s assessment is correct. But I may never know the answer.
6. Elevate.
Sometimes harassers are subject to various sources of discipline besides the law itself. A number of professions, ranging from doctors to mental health providers to lawyers, are bound by profession-specific rules of conduct. A few of my harassers turned out to be attorneys. An examination of the rules of professional conduct in the states where one of them is licensed–followed by consultation with a couple of legal ethicists and an attorney staffing the ethics hotline–suggested that this attorney was in violation of multiple ethics provisions. And so I decided to file a formal complaint with the bars in the states where he is licensed.
I don’t know what will happen as a result of my complaint. Many state bars hesitate to stir up controversy, and attorney discipline is relatively rare. But I do feel that it is important for others closer to his situation to have knowledge of his online behavior so that they can make an informed decision about what to do.
7. Expose.
Disclosing the identities of anonymous or pseudonymous Internet posters–also known as “outing”–is one of the most controversial issues confronting the Internet today. One line of thinking is that cyberharassers deserve to live with their online behavior in the light of day. A contrary position is that we have a strong social interest in anonymous speech, and that a regular practice of outing would chill such speech.
I think there are particular ethical concerns associated with using technological means to expose an individual, particularly if you administer a website that ostensibly does not log IP addresses. In the interest of time, I’m not going to address that issue here, although I hope to write more about it later. It’s a completely different issue when a pseudonymous person has disclosed so much information about himself online that ignoring his real-life identity would involve willful blindness on the part of anyone who knows how to use google. It amazes me that someone who engages in racist and misogynistic behavior online would attempt to claim that the very people he is harassing owe him an ethical or moral duty to refrain from exposing him. Such an argument is intellectually incoherent. That is, I think it is ethically permissible to expose the name of a person who has engaged in unacceptable behavior online.
I thought about publishing the names of some of my harassers. Several colleagues, both within and outside the academy, urged me to do so, particularly with respect to my most persistent harasser, and particularly after they learned that he was a public defender. As one eloquently explained: “This person is a public servant with a very important job. His work has a very direct effect on the lives and freedom of his clients. Even if this person is struggling with a mental illness, if that illness is manifesting itself as bigotry, then it’s important that his clients, the courts and his employer know that.” Another agreed: “Out his ass. He is an officer of the court with duties and obligations to his ENTIRE community. People have a right to know. You do not control what is done with the information thereafter.” And another: “Public defenders have an incredibly important job and need to be held to incredibly high standards.”
I struggled with this decision for a long time. Ultimately, however, I decided against publishing the person’s name for the reasons I have already described. Without full information, I hesitate to expose someone else’s life to the permanent censure of the Internet. I see a fairly obvious irony in the situation: I am protecting the online reputation of someone who has shown nothing but contempt for me and many other women and people of color, and who has polluted my google search results with hateful and disparaging statements.
But ultimately I found Leo Traynor’s riveting account of his decision not to report an awful troll to the police enlightening. Justice is important, but so is mercy. And I would much rather someone improve his behavior and learn from his mistakes than the alternative.
I have enjoyed blogging about these important issues, and am grateful to the Feminist Law Professors blog for providing a platform for me to do so. I’ll continue to write about identity-based harassment, discrimination, and other issues both here and on my personal website.
* I have chosen not to link to, or to identify, the sources of the material I reference in this post because I do not want to drive traffic to websites that tolerate racial and sexual harassment. If you would like more information, please feel free to contact me.


Interesting and provocative post. I happened to read it just after I read this, and the combination gave me a lot to think about: http://blog.airbriteinc.com/post/68044998554/peter-shih-10-things-i-learned-about-being-hated
Pingback: Click (Dis)Like: Why Social Media Use Is Now A Professional Issue - Tenured Radical - The Chronicle of Higher Education